Installation des packages
Sur la machine de stockage des données
: MySQL-4.xx Sur la machine de stockage des données
: mysql-client_4.0.20-11_i386.deb
![]()
![]()
Sur la machine de
détection :
snort-2.xx
snort-mysql-2.xx
libmysql12-4.xx
libpcap0-0.7.xx
zlib1-devel-1.xx
MySQL-client-4.xx
MySQL-common-4.xx
libmysql12-4.xxSur la machine de
détection :
snort-common_2.2.0-1_i386.deb
snort-mysql_2.2.0-1_i386.deb
snort-rules-default_2.2.0-1_all.deb
libmysqlclient12_4.0.20-11_i386.deb
libpcap0.8_0.8.3-4_i386.deb
zlib1g_1.2.1.1-7_i386.deb
mysql-common_4.0.20-11_all.deb
mysql-server_4.0.20-11_i386.deb
libdbd-mysql-perl_2.9003-2_i386.deb
libmysqlclient12_4.0.20-11_i386.deb
Configuration des interfaces eth0 et eth1 sans adresse IP
Editez
le fichier /etc/sysconfig/network-scripts/ifcfg-eth0
: DEVICE=eth0 et /etc/sysconfig/network-scripts/ifcfg-eth1
: DEVICE=eth1 dans /etc/sysconfig/network-scripts/ifcfg-eth2
(coté serveur MySQL) : DEVICE=eth2
![]()
BOOTPROTO=static
IPADDR=0.0.0.0
NETMASK=0.0.0.0
ONBOOT=yes
BOOTPROTO=static
IPADDR=0.0.0.0
NETMASK=0.0.0.0
ONBOOT=yes
BOOTPROTO=static
IPADDR=172.16.0.2
NETMASK=255.255.255.0
NETWORK=172.16.0.0
BROADCAST=172.16.0.255
ONBOOT=yes
| Editez le
fichier /etc/network/interfaces :
auto lo auto eth0 auto eth1 auto eth2 |
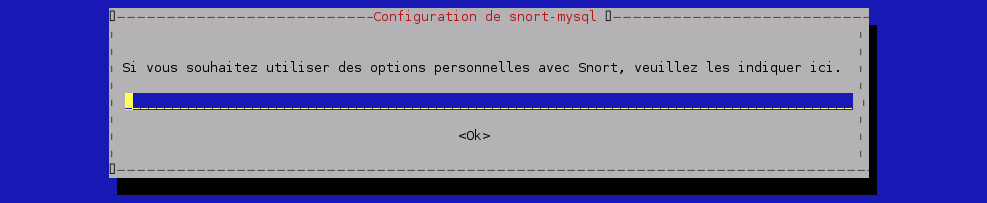
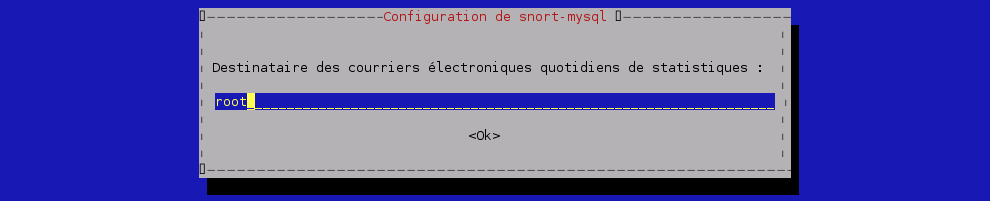
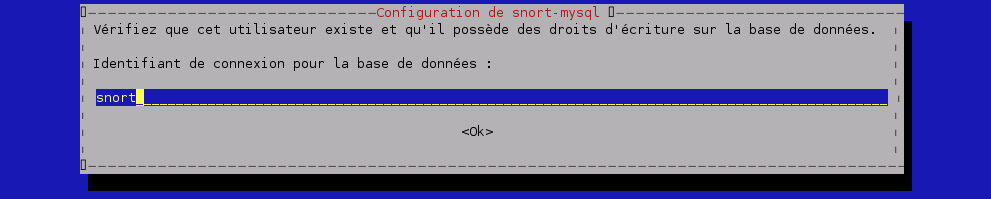
Installation de Snort-mysql :
|
Configuration de Snort
Sur la machine de détection, éditez le fichier /etc/snort/snort.conf pour modifier :
# Dans
l'exemple d'implantation, snort analyse deux branches réseau.
# Masque en /16 pour couvrir les réseaux 192.168.x.x
var HOME_NET 192.168.0.0/16
var EXTERNAL_NET any
#
Configure your server lists. This allows snort to only look for attacks
# to systems that have a service up. Why look for HTTP attacks if you are
# not running a web server? This allows quick filtering based on IP addresses
# These configurations MUST follow the same configuration scheme as defined
# above for $HOME_NET.
# List of DNS servers on your network
var DNS_SERVERS 192.168.0.0/24
#
List of SMTP servers on your network
var SMTP_SERVERS 192.168.0.0/24
#
List of web servers on your network
var HTTP_SERVERS $HOME_NET
#
List of sql servers on your network
var SQL_SERVERS $HOME_NET
#
Ports you run web servers on
var HTTP_PORTS 80
#
Ports you want to look for SHELLCODE on.
var SHELLCODE_PORTS !80
...
#
Path to your rules files (this can be a relative path)
var RULE_PATH /etc/snort/rules
...
#
[Unix flavours should use this format...]
output alert_syslog: LOG_AUTH LOG_ALERT
#
database: log to a variety of databases
# ---------------------------------------
# See the README.database file for more information about configuring
# and using this plugin.
#
output database: log, mysql, user=snort password=snortpassword dbname=snort
host=ids2.alex.fr
...
Copiez le script S99snort de la contrib vers /etc/init.d/snortmysql : [user@ids1
snort-2x]$ su
|
Sur la machine de stockage :
Créer la base snort dans mysql, copiez le répertoire /usr/share/doc/snort-2*/ du PC ou vous avez installé Snort vers celui ou fonctionne MySQL (sur disquette ou SSH) dans /usr/share/doc/ par exemple.
Si vous n'avez pas encore créé votre mot de passe root pour MySQL
[user@ids2 user]$ mysql
mysql> SET PASSWORD FOR root@localhost=PASSWORD('mysqlpassword');
mysql> SET PASSWORD FOR root@ids2.alex.fr=PASSWORD('mysqlpassword');
mysql> exit
Bye
Nous allons créer la base snort puis configurer les droits et mot de passe pour snort en localhost et ids2.alex.fr
[user@ids2 user]$ mysql -u root -p
Enter password: mysqlpassword
mysql> create database snort;
mysql> grant INSERT,SELECT on root.* to snort@localhost;
mysql> grant INSERT,SELECT on root.* to snort@ids2.alex.fr;
mysql> SET PASSWORD FOR snort@localhost=PASSWORD('snortpassword');
mysql> SET PASSWORD FOR snort@ids2.alex.fr=PASSWORD('snortpassword');
mysql> grant CREATE, INSERT, SELECT, DELETE, UPDATE on snort.* to snort@localhost;
mysql> grant CREATE, INSERT, SELECT, DELETE, UPDATE on snort.* to snort@ids2.alex.fr;
mysql> grant CREATE, INSERT, SELECT, DELETE, UPDATE on snort.* to snort;
mysql> exit
Bye
Créer la table snort dans mysql : [user@ids2 user]$ cd /usr/share/doc/snort-2*/
[user@ids2 snort-2x]$ bzcat snortdb-extra.bz2
| mysql -u root -p snort |
Vérifiez si tout c'est bien
passé :
[user@ids2 snort-2x]$ mysql -u root -p
>Enter password: mysqlpassword
mysql> SHOW DATABASES;
+----------+
| Database |
+----------+
| mysql |
| snort |
| test |
+----------+
3 rows in set (0.00 sec)
mysql> use snort
Database changed
mysql> SHOW TABLES;
+------------------+
| Tables_in_snort |
+------------------+
| data |
| detail |
| encoding |
| event |
| flags |
| icmphdr |
| iphdr |
| opt |
| protocols |
| reference |
| reference_system |
| schema |
| sensor |
| services |
| sig_class |
| sig_reference |
| signature |
| tcphdr |
| udphdr |
+------------------+
19 rows in set (0.00 sec)
mysql> exit
Bye
Source : http://www.snort.org/
Copyright © 04/02/2004, Arnofear

|
Ce document est publié sous licence Creative Commons Paternité - Pas d'Utilisation Commerciale - Partage des Conditions Initiales à l'Identique : http://creativecommons.org/licenses/by-nc-sa/3.0/deed.fr |